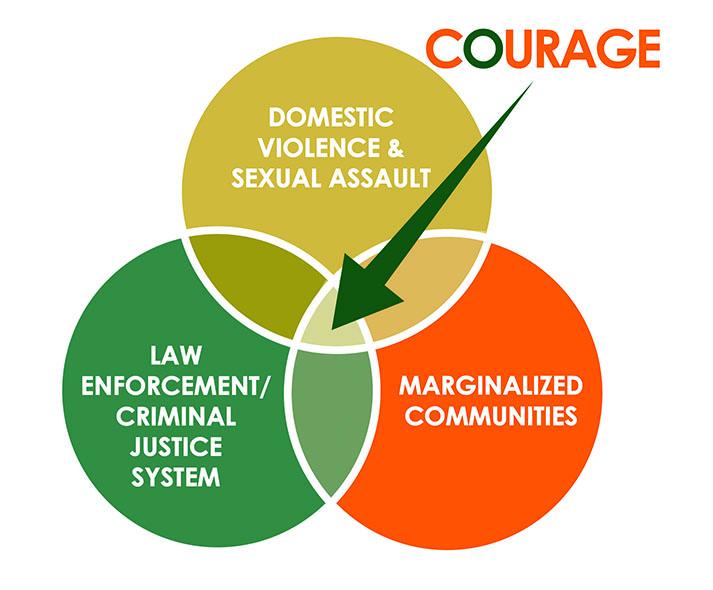
Special Collections
VAWnet's Special Collections are organized lists of select resources on specific topics related to gender-based violence that provide contextual information to encourage critical analysis. Collections are developed by the National Resource Center on Domestic Violence in collaboration with consultants and partner organizations. All collections are subjected to a peer-review process where seasoned advocates, academics, and other professionals in the field with particular expertise in the issue at hand are invited to provide input and recommend resources.
Special Collections are organized lists of select resources on specific topics related to gender-based violence that provide contextual information to encourage critical analysis.
Published: November 2024New Resources Added: October 2024
Published: January 2022
Published: June 2019
Published: November 2017New Resources Added: January 2018